Although remote access via telnet protocol is highly discouraged by most system administrators, there are still fans and old boys who are reluctant to change.
Interestingly, these people (who I’ve been dealing with) are all Windows users, i.e. they either use Windows at most of the time or they never have their hands on Linux at all.
So, I guess these people will only abandon telnet client when Microsoft start to bundle Secure Shell (SSH) clients with Windows OS :-(
Now back to topic, if you really want to put the Linux host at risk by allowing telnet protocol, here is the way to enable telnet server in Red Hat Enterprise Linux system (in case you’re asking).
Next, we look at How to enable root account telnet to Red Hat Linux system, if you have nothing to worry about system security (because you’re sysadmin, not security administrator :-)
Telnet client transmit account password in plain text format over (vulnerable) network. Thus, by default, Red Hat Linux (and most Linux distributions, I believe) disables telnet daemon and disallow root user to login directly via telnet protocol.
When you telnet to RHEL server with root ID, it will always rejects with message saying “Login incorrect”, no matter how many times you’ve entered the correct root password:
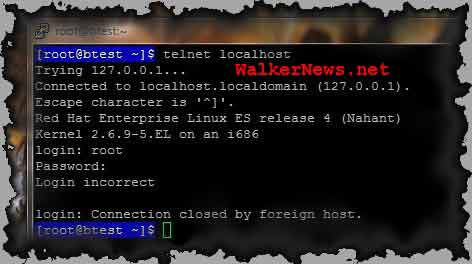
To overcome this “problem”, simply open /etc/pam.d/remote and remark this following line, where the PAM modulepam_securetty.so disallows root user login remotely via telnet and the alike (except SSH).
Original /etc/pam.d/remote with this line:
auth required pam_securetty.so
Tweaked /etc/pam.d/remote that remark (comment out)pam_securetty.so:
# auth required pam_securetty.so
This guide has been tested successfully on system running RHEL4. It should be valid for use in other Linux distributions that implement Linux-PAM modules (Pluggable Authentication Modules for Linux).


 留言列表
留言列表


